Evina questioned one of our experts to share some cyber tech insights with you. Maxime INGRAO, Security Analyst tells us all about Joker, the malware everyone is talking about.
What is Joker?
Joker is a malware. A malicious app that makes purchases through carrier billing.
Which apps does Joker infect ?
The Joker malware infects numerous malicious apps. Most of them are utility apps, image filter apps, wallpaper apps, and also anti-virus apps.
What type of malware is Joker?
Joker is a classic-type malware, it is executed locally after having been downloaded on the Google Play Store.
If it is a classic malware, why is everyone speaking about it?
Well, it’s a very comprehensive malware. It knows how to read and write SMS messages, and how to steal information and contact lists from users. It targets specific and numerous countries at once. The Joker malware is the perfect representation of fraud on apps.
Were there any victims among Evina’s clients?
No. While several anti-fraud solutions are based on a blacklist, Evina DCBprotect is different. We don’t rely on a list of malicious apps, we detect fraud types and block fraud mechanisms. In other words, we search for fraud’s DNA. Evina detected and blocked 5M+ payment attempts/transactions labeled as the Joker virus, and our clients have been informed right away.
How is it possible to have malicious apps displayed in the Google Play Store?
There are several techniques… when it comes to the Joker malware, the fraudulent code is downloaded on a server, then written after the app launches, so when Google Play receives the app and checks it, the fraudulent code doesn’t show.
So, how did Evina DCBprotect detect it?
The mechanism used by Joker had been identified in other malware through our mobile honeypot. Our honeypot mobile is a system that constantly installs malicious applications, decompiles and analyzes them to give us behavioral patterns to identify and block.
What is worth knowing about this malware?
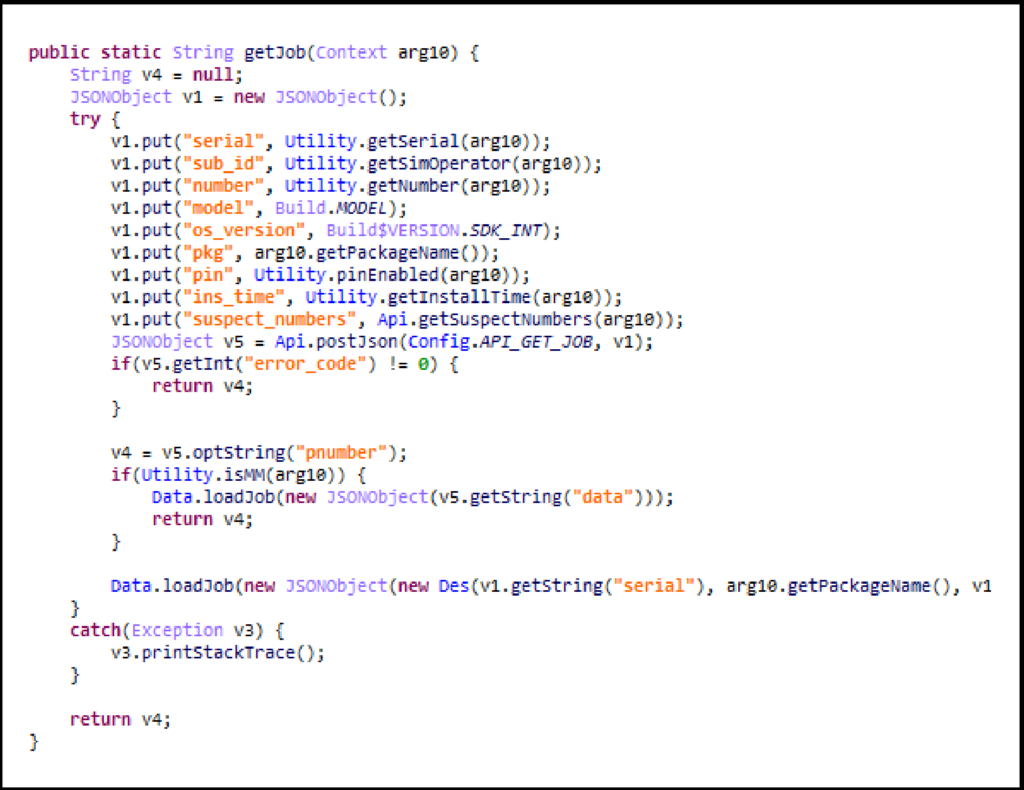
First of all, the malware makes the web page invisible to the victims and clicks on the purchase button without victims being aware. In order to hide the attack, the malware modifies the x-requested-with header. Last but not least, the app grabs phone numbers and compares them to a suspect numbers database created by the fraudster to assess whether to attack.
A final word?
Joker is the buzz of the moment, but there have been and there still are a lot more harmful and sophisticated malware targeting carrier billing. We are experts in carrier billing and 100% anti-fraud focused. In the last 24 hours, we’ve protected our clients from 91 358 fraudulent transactions.
Who is Maxime INGRAO?

Security Analyst at Evina, Maxime leads the malware research, reverse engineering and security web conception. Passionate of hacking, Maxime decided from a young age to focus on cybersecurity. As a teenager, he created a community website gathering 1500+ members around cybersecurity. He started his professional path in web development before fully working in cybersecurity.
