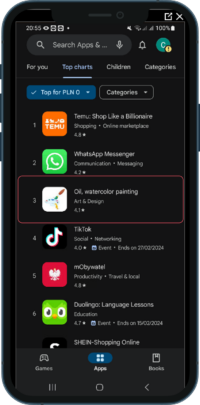
In February 2024, Evina's cybersecurity experts uncovered Aesimus, a novel malware variant from the Autolycos family, operational and concealed within Poland's top three downloaded apps. This rare and sophisticated discovery highlights the rise in power of malware in today's digital cybercrime.
Evina, a global leader in cybersecurity, has unveiled the discovery of a new malware variant named Aesimus. This latest variant, emerging from the Autolycos malware family, was detected in February 2024 by Evina’s team of malware experts. Aesimus stands out for its novel and sophisticated operational method and virality. It has swiftly climbed the ranks to become one of the top three downloaded apps in Poland, which highlights once again that the malware threat does not concern an isolated audience with “at-risk” behavior who download apps from outside the official app stores.
Aesimus employs a unique technical strategy to conceal its malicious code. By hiding behind an image URL in creative apps, the malware executes its operations discreetly, bypassing traditional security measures. This innovative method allows Aesimus to covertly subscribe unsuspecting mobile users to premium services through Direct Carrier Billing (DCB), diverting funds without detection.
Download the full report on the newly discovered malware Aesimus here.
Another key strategy is that not everyone who downloads the application will be defrauded. Cybercriminals select their victims by launching clickable ad campaigns aimed at specific audiences (e.g. based on age, socio-economic profile, networks used) who are then redirected to the official Play Store to download the application. They are then tracked (deeplink technique) and it is they who are defrauded. Why this process? To remain discreet, to target the most vulnerable people who are least likely to complain, to regulate the flow of fraud so as not to be identified!
Evina’s findings reveal that Aesimus has already launched over 1 million fraudulent attempts, with more than 500,000 users inadvertently downloading the infected apps. Four applications harboring the malware have been identified, with one notably surpassing TikTok to secure a position in the top three apps in Poland. This unprecedented attack has targeted all Polish mobile operators, underlining the urgency of addressing this threat.
David Lotfi, CEO of Evina, commented on the discovery, stating, “Once again, we see the professionalization and technicalisation of mobile payment fraud at work. A well-crafted rogue app quickly rises to the top of a country’s app rankings, and by selectively targeting the audience they are going to defraud, through advertising as in this case, cybercriminals ensure that they do not arouse the suspicions of traditional security players.” The revelation of Aesimus not only highlights the evolving landscape of cyber threats but also underscores the critical role of advanced cybersecurity measures. Evina, with its fraud-preventing presence in over 80 countries, leverages AI technology and information-sharing partnerships with telecom companies to identify and neutralize malware more effectively and swiftly than ever before.
The discovery of Aesimus and its subsequent analysis reflect Evina’s commitment to safeguarding the digital ecosystem. By reverse-engineering and unmasking malware hidden in app stores worldwide, Evina’s team of specialist cybersecurity experts continues to provide defense to its partners against the increasing sophistication of cybercriminals.
About Evina
Evina offers the most advanced cybersecurity technology for carrier billing and mobile money. Evina’s solutions increase revenues and decrease complaint rates by protecting +20 million transactions in +80 countries each day. The global company boasts over 19 nationalities and has offices in Paris and Dubai. Evina received the Golden award for Best Financial Clearing Solution in 2021 from Juniper Awards and Best DCB Anti-Fraud Solution in 2020, 2021 and 2022 at the Global Carrier Billing Summit. More info at: https://www.evina.com/
Evina’s press contact: [email protected]