DCBprotect
Block Technical Fraud on Carrier Billing
DCBprotect increases revenue and decreases complaints for MNOs, merchants, and payment aggregators, by protecting all payment flows from the advertising banner to the payment confirmation page.
Request a demo
Carrier Billing is a massive opportunity plagued by fraud
Carrier billing offers booming business opportunities.
- There are 4.7 billion mobile phone users worldwide.
- Mobile purchases are worth 3 trillion dollars and increase by 25% each year.
- Carrier billing is one of the easiest payment methods, with high conversion rates.
- Transactions on carrier billing went from 11 to 44 billion dollars since 2017.
But massive fraud is causing many difficulties to insufficiently protected players.
- Fraud is the major unaddressed culprit of damages to the brand image.
- Complaint management has a high cost in terms of time and money.
- Fraud prevents the implementation of one-click payments.
- MNOs are hindered from becoming major players in mobile payment.
- Profitable traffic sources remain inaccessible.
- Innocent players risk fines and service cuts.

We block fraud,
you focus on your business
For mobile network operators
- Improved brand image
- Less complaints
- More revenue
- Optimized conversion flows
- New business opportunities
For merchants & payment aggregators
- More revenue
- More efficient payment flows with better conversion rates
- More profitable traffic sources
- New and better partnerships
99.94%
fraud attempts detected
0.06%
false positive rate
<100ms
latency
All types of fraud detected, even the newest and most sophisticated
Remotly controlled fraud
A malware takes control of a device to make fraudulent payments.
Clickjacking
The user is tricked into clicking on a hidden payment button, that is disguised as a different button to the eyes of the user.
Spoofing
The theft of the network/SIM identity of users to make a payment on their behalf.
Code injection
Malicious code is injected through a browser flaw to make an unauthorized automatic payment, that is billed to the user.
Malicious app
A mobile application that secretly contains malware, programmed to go through all the steps of the flow in place of the final user to make payments without asking for the user’s consent.
Bypass
Short circuits process flow to make payments without clicks.
Replay attack
Transmissions are intercepted and repeated maliciously to make payments.
Easy integration on all kinds of payment flows
- Protection of your payment page.
- Protection of the page you host that leads to the payment page.
- Protection of redirections.
- Protection of pages hosted by your partners.
A fully GDPR compliant solution
- DCBprotect does not store any personal data.
- DCBprotect is not considered a data controller or a data processor.
- Data used, processed and stored during all flows are the minimum required to ensure the service functioning.
Monitor and analyze your traffic, on personalized dashboards
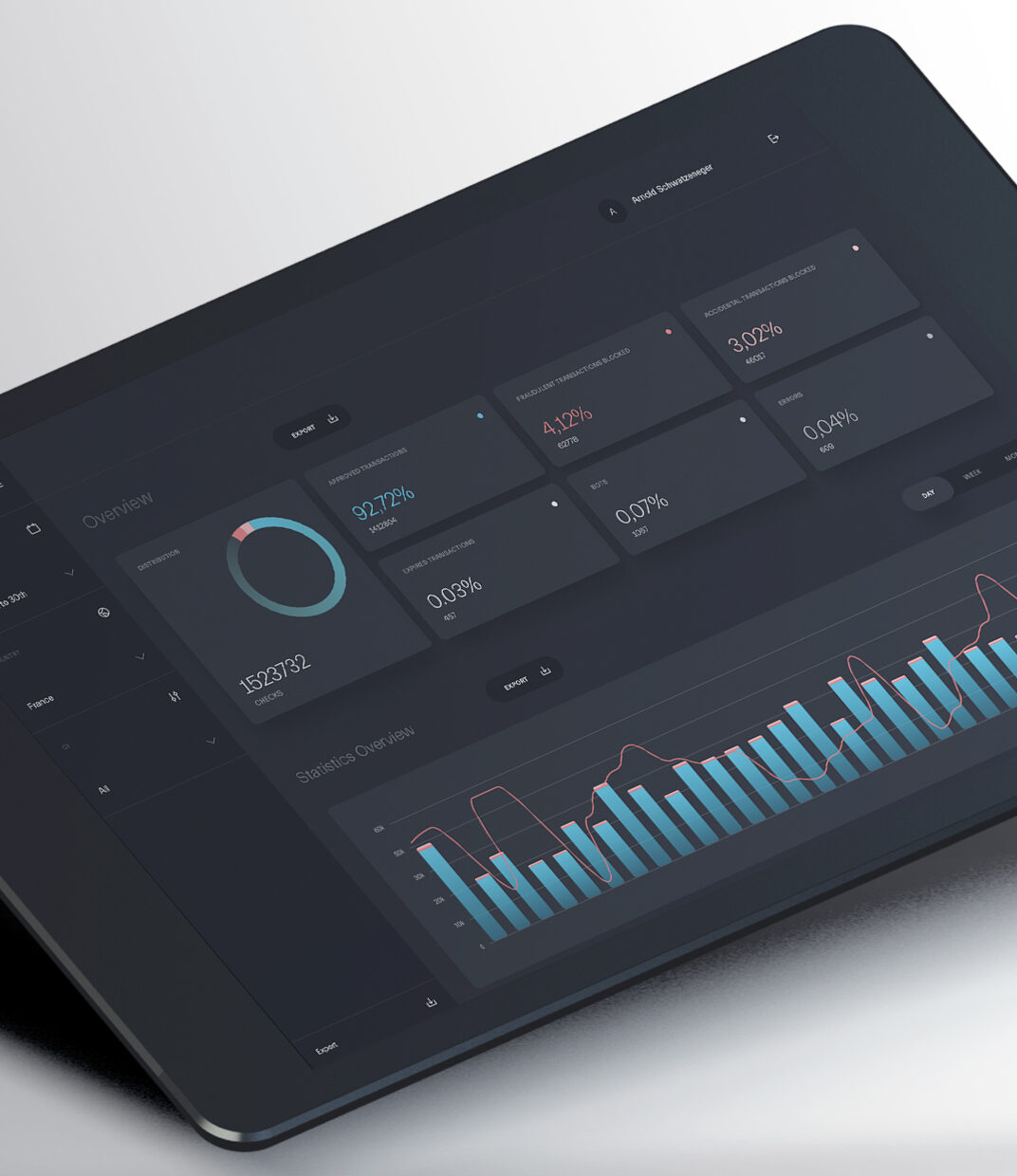
- In real-time
- Dedicated personal access
- Training session
- Downloadable and shareable data
- Fully customizable data
- Customized alerts
Developers we’ve thought of you too!
- Fastest deployment
- Works with any infrastructure
- Dedicated engineer support
- Personalized onboarding
Evina
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
~
package main
Import (
"fmt"
"net/http"
"io/ioutil"
)
func main() {
url := "http://api.dcbprotect.com/username/script?adc=0&so=false&cjv=false"
req, _ := http.NewRequest("GET", url, nil)
req.Header.Add("Accept", "application/json")
res, _ := http.DefaultClient.Do(req)
defer res.Body.Close()
body, _ := ioutil.ReadAll(res.Body)
fmt.Println(res)
fmt.Println(string(body))
}
Ready to decrease fraud and increase revenue?
Request a demo with one of our team members.